Repairing Shdoclc.dll Errors
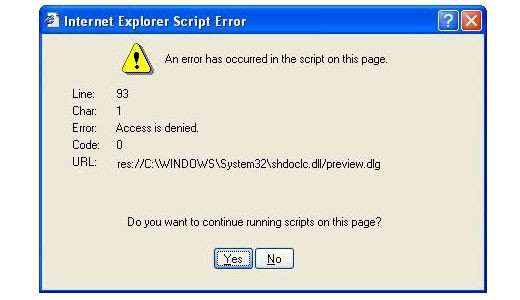
The shdoclc.dll, which stands for Shell Document Object and Control Library, is a resource file that is used primarily by Internet Explorer for the purpose of storing specific items, such as dialog boxes, menus and various other components that make up this program. These particular error messages may appear while you are installing or using an application, when Windows first boots up or just before it’s about to shut down, or even while installing Windows for the very first time.