| Attention Before you read this post, I highly recommend you check out my resources page for access to the tools and services I use to not only maintain my system but also fix all my computer errors, by clicking here! |
Malicious attacks and online scams continue to grow as each day passes. As a result, this puts all our confidential details at risk, whether it be our social contacts, login credentials, etc.
Online privacy is of a much bigger concern today, with many new laws introduced in this area, especially in the EU. Because of this new reality, a few developers came together and created Hidden Toolbox, to allow end users to surf the internet privately. In this post, I will be reviewing this product, to confirm whether or not Hidden Toolbox can protect you from the many pervasive issues on the internet.
What Is Hidden Toolbox?
Hidden Toolbox is basically a privacy tool that was designed to allow you, the end user, to hide videos, images and files and even the tool itself, so that your system would appear clean of such activities.
Once you have imported your files over to the program, you can organise them based on several factors, like tags and categories. Hidden Toolbox has a number of features so that you can surf the web without leaving a trace and a media player, which will allow you to listen to your favourite songs or view images, in secrecy. It also features video bookmarking, which you can use to quickly access your favourite videos.
It’s essentially a secret tool that, no one who has access to your computer will be aware even exists, and in the event that your system is compromised you can quickly destroy all its data, remotely and uninstall the tool, without anyone being the wiser.
Security and Privacy
Privacy is very important, which is why, all files stored on the program, remain on your system, none of it is sent to any cloud service, where it could potentially become compromised. All contained data is also encrypted and hidden, so no one can find it or access it. In addition to making your personal files hidden, the developers felt making the tool visible, wasn’t the best, so they hid that also, behind a secret combination of keys and a password that he/she would have to know to access the program.
 Hidden Toolbox is an ALL-IN-ONE Privacy and Security tool. For access to this tool, click the link below: |
Hidden Toolbox Review: Features
I’ve already touched briefly on the many features that Hidden Toolbox has to offer. But for a complete rundown of all the features that I think standout most, I suggest you read the following:
 | Secret Internet Browser: This feature allows you to surf the internet anonymously, while end users are given the option of importing their bookmarks from their other browsers.. |
 | Integrated Popup Blocker: With the forever increasing number of ads on website these days, a popup blocker is a must. |
 | File Organizer: Hidden Toolbox has a built in organiser, which you can use to organise and categorise your systems data. |
 | Hidden Media Player: With Hidden Toolbox’s built in media player, you can play a plethora of media file types, all without leaving a trace. |
 | Video Bookmarks: A unique feature which allows you to bookmark favourite parts of your videos, so that you can access them in an instant. |
 | Built-in Search: This feature will allow you to locate any and all files present on your hard drive. |
 | Playlists: Create your own video or image playlists. |
 | Panic Button: It’s a button, which allows you to quickly close Hidden Toolbox. |
 | Virtual Keyboard: With this virtual keyboard, keg loggers will no longer be able to record your button presses. |
Hidden Toolbox, is what it says, a toolbox, which comes with everything that you would ever need. During its developmental stages, it started off, initially as a tool for hiding your files, and then it grew, as users demanded more features, such as the ability to privately surf the internet. When an end user surfs the web or plays a particular video file or views an image, all of this needs to be done, without leaving any record of this activity, this is what Hidden Toolbox does.
An end user may have thousands of different files on their system, and it make life easier for them, if they were able to quickly access these files. That mind-set, was the motivation behind the file organiser, which you can use to arrange your data, and which the search scanner will use, when following up on your queries.
Once the developers of Hidden Toolbox started adding new features to their tool, they were compelled to keep going, and this led to the introduction of the video bookmarker, which is definitely a unique feature in its own right.
My Experience
When I installed the program, for the very first time, I was given a quick rundown of how the program works, and how to access it.
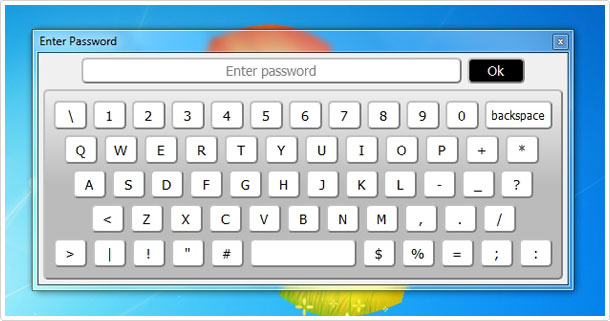
The Hidden Toolbox is installed on your computer, but there is no way of accessing it, but through a quick combination of keys that you must press whenever you want to load up the program. Once you press these keys, a virtual keyboard will appear, prompting you to type in your password.
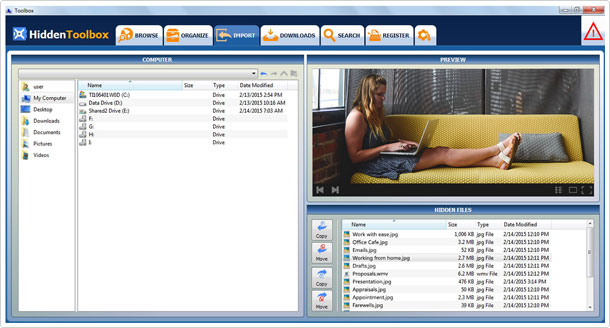
Hidden Toolbox allowed me to import my files to it, which were saved in a specified location, one established during setup. This information was then accessible, whenever I wanted it.
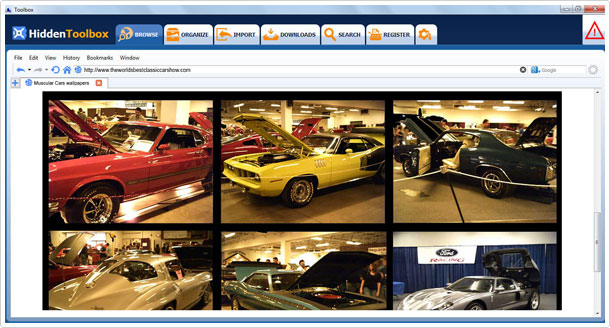
The program has a number of buttons and features that are visibly apparent, but everything is laid out in a very simple fashion, so it never at any point seems complicated or sophisticated. There’s a Panic button, which you can use to hide the tool, after or during use. This feature is especially useful, if you use the tool on a system that has multiple users.
The program itself, is installed in a hidden location, which I was unable to find. Which is a good thing, as it ensures that no one can simply open up the tool, without knowing the secret combination + password.
The program comes with an internet browser, which is the first thing you see. 256-bit SSL file encryption is used; which is the new standard nowadays. Hidden Toolbox conceals its presence on your system, which means, anyone that has access to it, whether legitimately or illegitimately, will not be able to keep track of the various activities you carry out while using the tool. However, the tool does not conceal your IP address. If you would like to surf anonymously, I’d imagine you’d have to combine this tool with a VPN.
What I Like
The things I liked most about this tool, include the following:
 | It uses 256-bit SSL encryption. |
 | It allows you to important files to it, which you can then conceal from others, who have access to your system. |
 | The web browser is competent and fast. |
What I Didn’t Like
The things I didn’t like about it or I feel could improve Hidden Toolbox, includes the following:
 | It doesn’t have its own VPN feature. |
 | You cannot add extensions to its browser. |
 | Colour scheme and theme looks a little outdated. |
Conclusion
On paper, this Hidden Toolbox seems rather complex, with a wide range of features and capabilities, but in practice, it’s a very simple tool, which allows you to carry out a range of tasks, anonymously. Hidden Toolbox is as much a security tool as it is a privacy tool.
Would I recommend it, though? I’d say it depends. Hidden Toolbox is probably best suited for systems that have multiple users. If you’re an adult who owns a family computer and there are a several tasks that you would like to be able to do on it, without anyone else knowing about it, then this is your tool.
 Hidden Toolbox is an ALL-IN-ONE Privacy and Security tool. For access to this tool, click the link below: |
| Review Overview | |
| Features | |
| Ease of Use | |
| Installation | |
| Customer Support | |
| Hidden Toolbox is a feature-rich, yet simple, privacy and security tool. |
RECOMMENDED |
Are you looking for a way to repair all the errors on your computer?

If the answer is Yes, then I highly recommend you check out Advanced System Repair Pro.
Which is the leading registry cleaner program online that is able to cure your system from a number of different ailments such as Windows Installer Errors, Runtime Errors, Malicious Software, Spyware, System Freezing, Active Malware, Blue Screen of Death Errors, Rundll Errors, Slow Erratic Computer Performance, ActiveX Errors and much more. Click here to check it out NOW!

